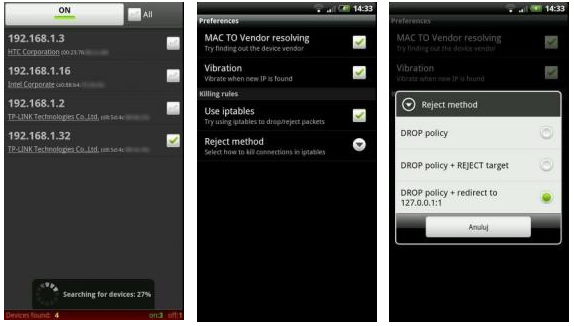
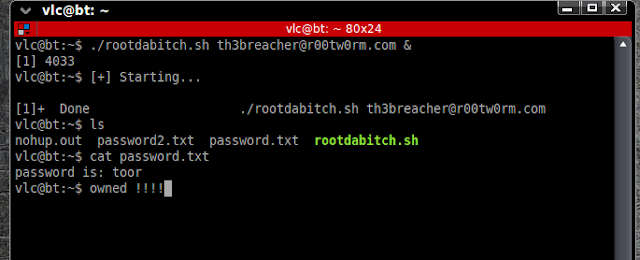
IP addresses you should never scan
US GOVT IP ADDRESSES YOU SHOULD NOT SCAN ---------------------------------------- RANGE 6 6.* - Army Information Systems Center RANGE 7 7.*.*.* Defense Information Systems Agency, VA RANGE 11 11.*.*.* DoD Intel Information Systems, Defense Intelligence Agency, Washington DC RANGE 21 21. - US Defense Information Systems Agency RANGE 22 22.* - Defense Information Systems Agency RANGE 24 24.198.*.* RANGE 25 25.*.*.* Royal Signals and Radar Establishment, UK RANGE 26 26.* - Defense Information Systems Agency RANGE 29 29.* - Defense Information Systems Agency RANGE 30 30.* - Defense Information Systems Agency RANGE 49 49.* - Joint Tactical Command RANGE 50 50.* - Joint Tactical Command RANGE 55 55.* - Army National Guard Bureau RANGE 55 55.* - Army National Guard Bureau RANGE 62 62.0.0.1 - 62.30.255.255 Do not scan! RANGE 64 64.70.*.* Do not scan 64.22